As a SaaS development company, Devtorium has been working on our proprietary AI-powered platform Marquètte. We’ve been fascinated by the incredible opportunities the marketing software industry presents. So Marquètte is a product that aims to make top-grade marketing services more accessible to everyone. Now we can say that our efforts have been recognized. SuperbCompanies.com, a trusted portal that lists the best IT & marketing companies, included Devtorium in its Top Mobile App Marketing Companies rating for 2022.
We are very proud that Marquètte and Devtorium got this acknowledgment from a highly reputed IT ranking portal.
Devtorium keeps growing and expanding the list of services we offer beyond custom software product development. At the moment, our team includes highly qualified professionals that specialize in the following:
- Custom Software Development
- MVP/Product Development
- Low-Code & No-Code
- Cloud Migration Consulting
- Software QA Testing & Automation
- UI/UX Design
- Data Science
- Information Security Services
- Mobile App Development
- eCommerce
- SaaS Development
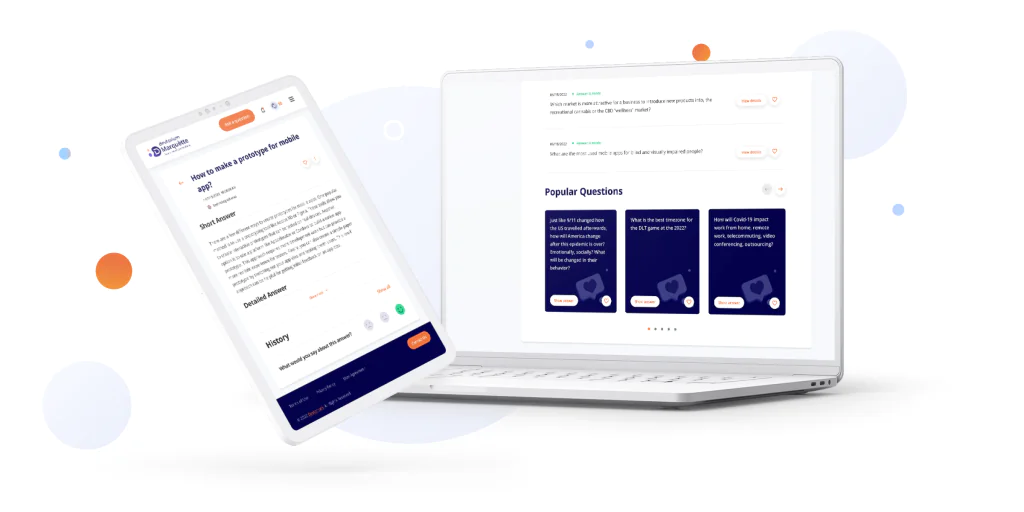
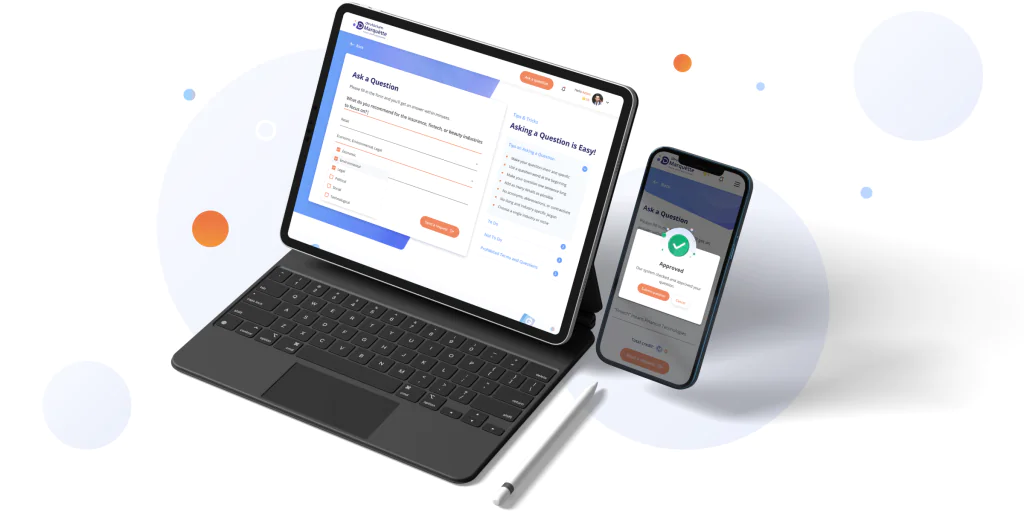
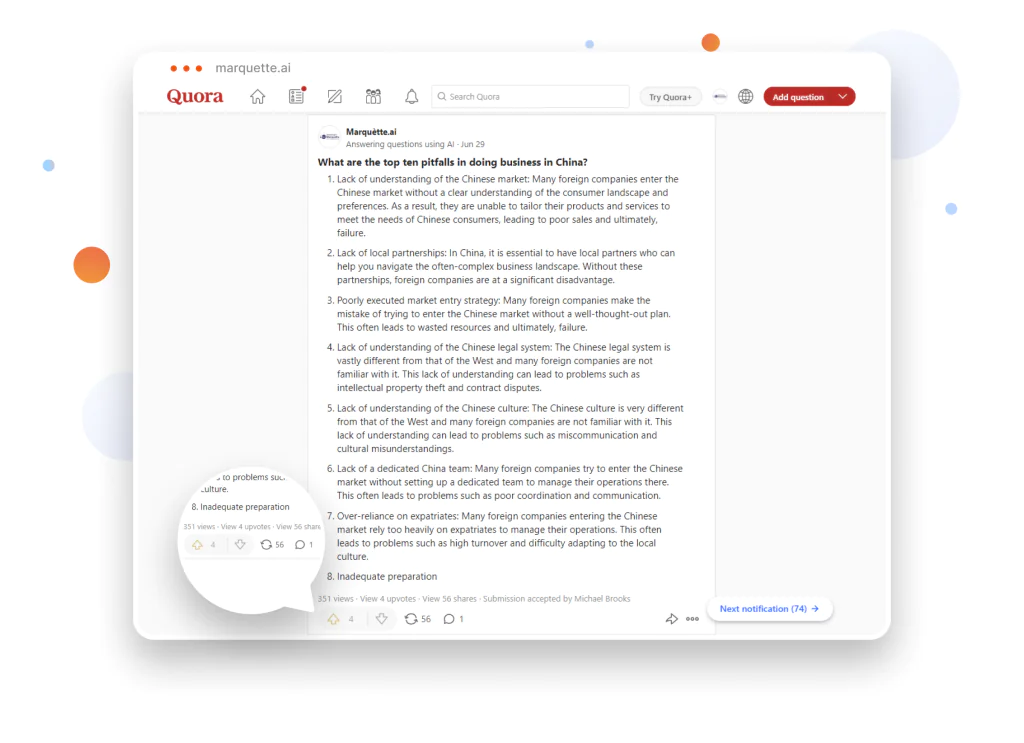
We are working on expanding this list and, of course, developing Marquètte further. At the moment, this is a piece of AI content writing software that can help both professional copywriters and businesses that can’t afford to hire a full-time writer for their content marketing.
However, our plan as a SaaS development company includes expanding this platform to become an intelligent assistant to a business owner or entrepreneur. In the future. Marquètte will help conduct research, generate content, and make business decisions by offering data-powered opinions from AI.
How SaaS Development Company Devtorium Got on SuperbCompanies.com
SuperbCompanies is a service that helps clients find the best providers of IT services worldwide. Professionals working for SuperbCompanies have over ten years of experience, and they spend their days collecting, processing, and analyzing information about various IT service providers.
Their research is extensive as they study every service the company provides. It means that, for example, if the company offers custom mobile app development and UI/UX design, they will investigate both of these services separately. This way, SuperbCompanies can provide customers with the most accurate information about every IT business in their database.
They evaluate IT companies based on such factors as:
- Quality
- Market presence
- Reliability
- Experience
- Portfolio
- Professionalism
- Customer service
- Awards
- Fair pricing
- Proven customer feedback
Most importantly, SuperbCompanies only the companies that show a high and consistent growth rate. In addition, the research is ongoing, so information is reviewed and updated monthly.
Marquètte currently is Devtorium’s foremost marketing app, but we have plans for many more. We are proud to be recognized by SuperbCompanies. We hope to see more of our services in their Top rankings soon!