The scope of information security services is extensive today, and Devtorium is proud to announce that we are expanding our offering in this area. Today, we are introducing our Information Security Team and explaining all the services we can provide to help protect your business on every level.
Let’s start with a quick recap: Devtorium offers a wide range of cybersecurity services to any business, regardless of industry. In addition to this, Morebis, a part of the Devtorium Group of Companies, holds the ISO/IEC 27001:2013 certification in the ISMS field. Moreover, this year, we became partners of the PECB Company. We can now conduct audits and provide training courses for those wishing to receive this ISO certification.
How Devtorium Information Security Services Can Benefit Your Business
Because Devtorium is a versatile team of professionals, we can offer multiple types of services to our clients. In regards to information security, we can help protect your business by providing the following:
- Comprehensive information security system audit
We can conduct a comprehensive study and analysis of your entire security system. Our audit covers everything, from the physical security of the building to the digital security of your products. - Threats and weaknesses investigation
Our specialists will identify risks and vulnerabilities while going through your entire security system. The report we provide after a thorough risk assessment will list all your weaknesses and potential threats so you can understand where the danger is. It will enable you to make better decisions when building or updating your security system. - Security system checklist
Devtorium specialists can provide you with a detailed checklist you can use to build a tight security system. The checklist is built based on our professionals’ investigation and custom-tailored to your company’s needs. - Security system design and setup
You can employ Devtorium information security services when building a security system from scratch or updating the one you have. In this case, our specialists will conduct an audit, provide a plan, and help guide you through every step of securing your business. - ISO/IEC 27001:2013 certification audit
Devtorium is now a certified company that can conduct an audit you need to receive your ISO 27001:2013 certification. We are also authorized to provide the training necessary to achieve this certification level.
Information Security Services by Devtorium: The Team
Today, we want to introduce you to some Devtorium Information Security Team members. This team comprises specialists in different areas, each with outstanding talent in their field. They work together to cover different areas of digital and physical business security.
Our team is young but includes outstanding people with many years of experience in their respective fields.
Nataliia Kashuba: Chief Security Officer/Deputy General Manager
The Head of Devtorium’s Information Security Department, Nataliia Kashuba, holds Cisco Networking Academy/CCNA Cybersecurity Operations, DPO and ISO 27001 SLA certifications. Nataliia is our foremost expert on information security services. Her job is to coordinate the team’s work at every level.
Moreover, Nataliia is also the founder of a charity fund that actively supports Ukraine’s defenders. They provide dehydrated homecooked meal packs to soldiers on the frontlines and work with volunteers to provide our forces with necessary equipment and meds.
From her position as Chief Security Officer, Nataliia takes on the leadership role when working with clients and developing a personalized strategy for each of them. She is also directly responsible for Devtorium’s security certification renewal and the growth of our services package in this niche.

Pavlo Kharchenko: Head of IT Department
The Head of Devtorium IT Department also actively participates in our Information Security Services Team. He holds the ISO 27001LA certification and has vast experience working with the documents necessary to achieve these certifications. Managing this area of security paperwork is his main focus in the team. The documentation that Pavlo audits covers everything from the company’s policies to instructions on keeping all their communication and offices secure.
Pavlo is also responsible for digital security within our own company and can offer these services to Devtorium clients. This part of his specialization covers:
- Ensuring that all communication within the company and with outside agents is secure on every level
- Monitoring and maintaining network security
- Developing and managing the procedures to ensure the physical security of the company’s offices and equipment
- Creating security protocols for working with third-party software and ensuring all such interactions are secure and the client’s data is protected

Anton Mikushyn: Head of QA Department
QA professionals make up a vital part of the Devtorium Information Security Team. Even the Head of our QA Department, Anton Mikushyn, plays an active role. As a part of the team, his responsibilities are:
- Projecting and implementation of secure architectures of applications to avoid security threats from the start
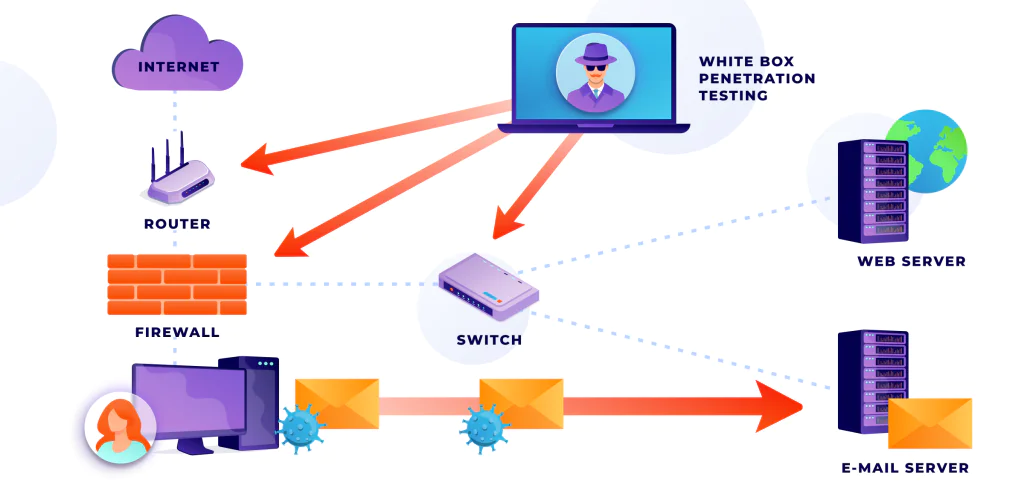
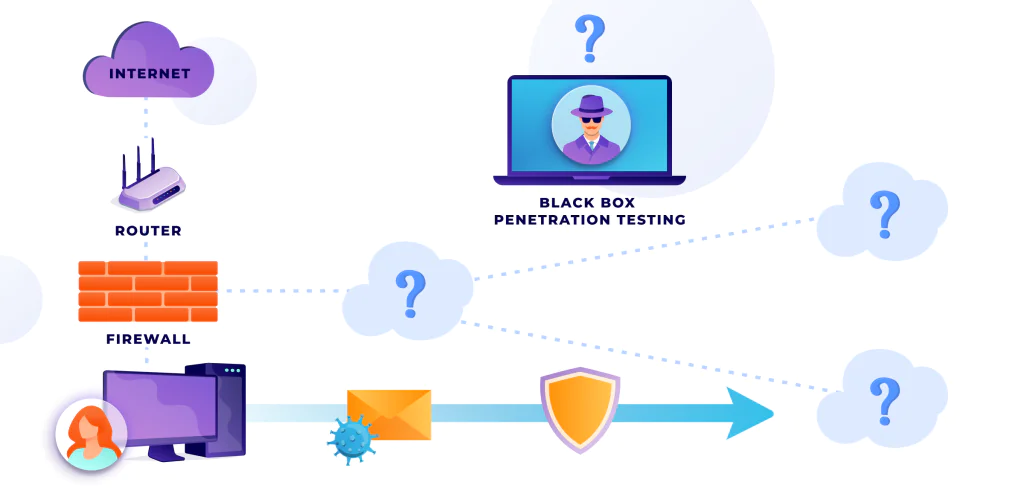
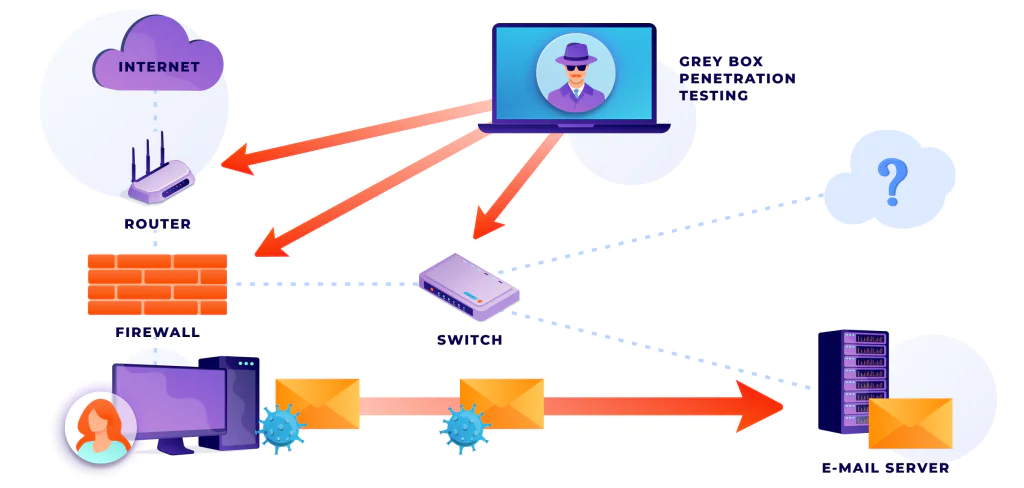
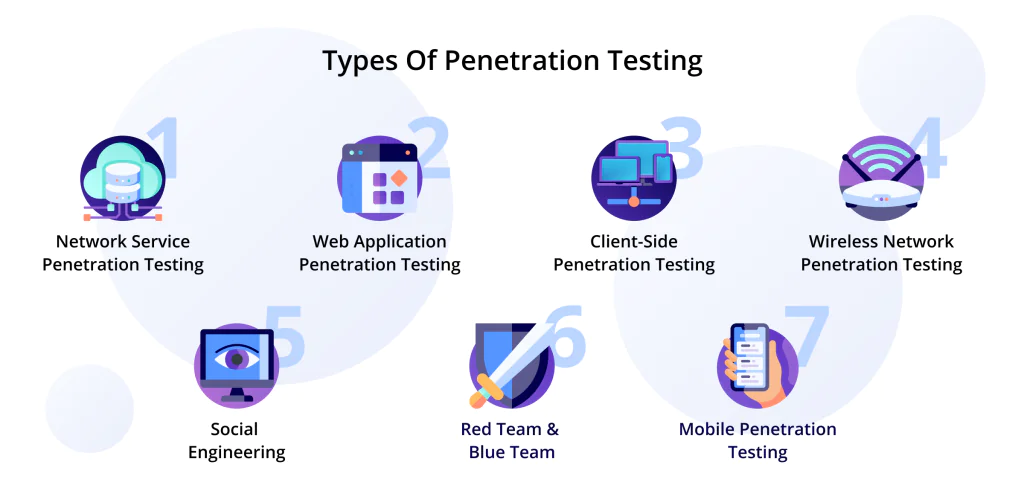
- Performing penetration testing to find and remove threats in applications
- Personnel education
- Creation and realization of security policies
- Organization of security monitoring for early identification and elimination of threats
- Research of new threats and technologies
- Reaction to security incidents, including analysis and recovery after incidents
- Attack scenarios development
- Evaluation of the acknowledgment level of employees in security areas and improvement strategy development
In regards to the relevance of information security today and his personal interest in the field, Anton had a lot to share:
This is a new and interesting area where I have a lot of space to grow, and it can be an additional technology that our company can handle as a developing area.
According to the latest situation in the world, information is essential, and its importance will keep growing in the future. I like to compare the real world with science fiction movies. For example, we were shown a world with electric self-driving cars (see I, Robot, Demolition Man, Blade Runner, etc.). Now, for the last ten years, vehicles with self-driving technologies have been mass-produced and are becoming the norm. Even the creation of a flying taxi is merely a question of time ( remember the 5th Element).
So it’s time to look back to Johnny Mnemonic, where loading information into an implant is safer than sending it via the web. Cybersecurity today is not about keeping someone’s data private but about keeping systems functional. Your systems must be able to communicate with other systems and recover after an attack. This area will broaden as the number of systems we use daily grows. Today, technology controls almost everything, starting from smart kettles and finishing with applications to run nuclear plants. So, security is paramount.

Nadiia Ovsiannikova: Senior QA Engineer
Another member of our Information Security Team from the QA side is a senior-level professional with 10+ years of experience, Nadiia Ovsiannikova. Nadiia started studying security as a personal interest because she enjoys learning everything connected to testing. Moreover, Nadiia understands that it’s imperative for everyone today to be aware of the dangers waiting for you online. Therefore, she wanted to know how to protect herself and quickly expanded this to teaching others in the company.
At the moment, Nadiia’s specialization in the team mainly concerns knowledge-sharing and penetration testing. Nadiia can use her experience in QA testing and understanding of contemporary security practices to implement various types of testing.

Dmytro Chernenko: Junior System Administrator/DevSecOps
Dmytro is one of the youngest members of the Devtorium Information Security Services Team, and he is one of the most motivated. He holds several certifications, including Cybersecurity Essential, CCNA Cybersecurity Operations, Get Connected, and NDG Linux. As a part of the team, he acts as a DevSecOps and is responsible for the following:
- Threat monitoring, classification, and evaluation of threat level
- Risk management
- Comprehensive systems monitoring
- Implementation of authentication and authorization systems
- Implementation of automated information security tools
Dmytro is developing fast in his career, and his plans for the near future include obtaining the CISCO Cybersecurity certification. His main ambition for now is to grow to the Security Architect position.
Devtorium Information Security Services: Plans for the Future
Devtorium continues its work in developing a wider offering of information security services to any business interested in protecting itself. We are also now able to help those who are looking to achieve their own ISO 27001:2013 certification. If you want to learn how we can help you, contact us for a free consultation.
More on the topic of cybersecurity from Devtorium: