Now is definitely the time to use AI in cybersecurity. In fact, those who don’t do this put their businesses at great risk. While some reports aren’t highly detailed, according to cybercrime statistics, the damage caused by it amounts to $12.5 billion. This number is growing every year because complex systems are inherently vulnerable, and criminals use every tech innovation they can. So, no one can afford not to use AI’s help to build the best possible security system while hackers use this technology to exploit your weaknesses.
Modern threats need up-to-date solutions. Devtorium offers a wide range of cybersecurity services, and our security and R&D specialists are working to identify the best AI applications in this area. At the current level of technology, AI can automate tasks, improve threat detection, predict future attacks, and more. In this blog, you will learn about the benefits and drawbacks of using AI in cybersecurity systems.
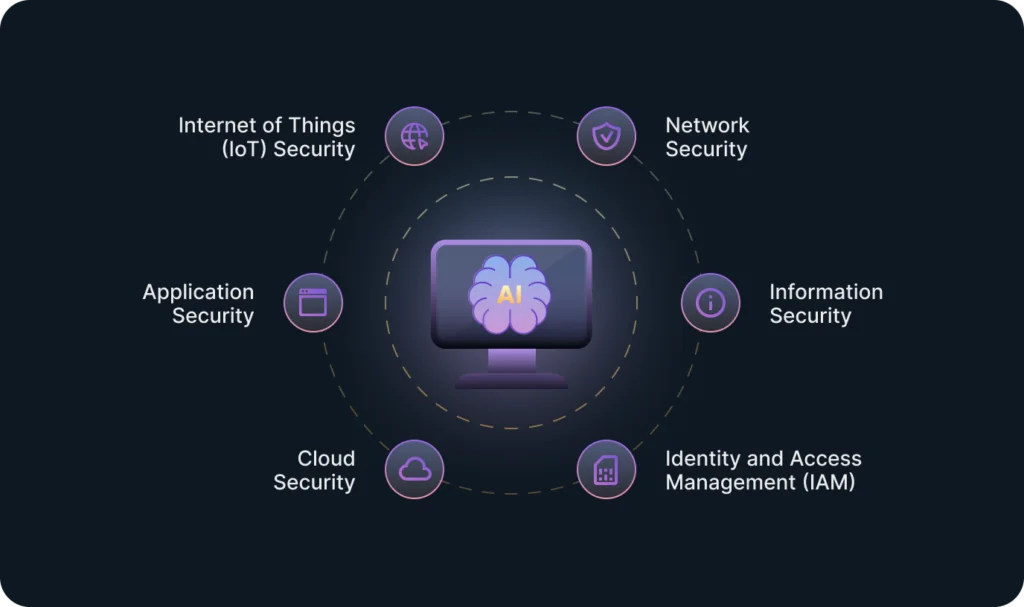
Use of AI in Cybersecurity: Applications in Various Systems
Network Security
This type of security protects a computer network from unauthorized access, misuse, or attacks. It involves developing a secure infrastructure for devices, users, and applications to work safely. The tools used in network security include firewalls, VPNs, and data loss prevention (DLP), as well as intrusion detection and prevention systems.
AI applications in network security:
- Anomaly detection.
AI can analyze network traffic patterns to identify unusual activity that might indicate a cyberattack. - Automated threat mitigation.
AI systems can automatically take steps to isolate threats, such as blocking malicious IP addresses or quarantining infected devices.
Information Security
This system protects digital information, such as data stored in databases, files, or other repositories. It includes data encryption, access controls, and data backup and recovery. Devtorium is an ISO/IEC 27001:2013-certified company and our specialists are able to ensure complete security of your systems both with and without AI.
AI use in cybersecurity of information systems:
- Data Loss Prevention (DLP).
AI can analyze data content to identify sensitive information and prevent unauthorized data exfiltration. - Threat intelligence analytics.
AI can collect and analyze threat data from various sources to predict future attacks and improve security planning.
Application Security
This security system aims to secure software applications from being stolen or hacked. Application security can reveal weaknesses at the application level, helping to prevent attacks. AI implementation in application security can include secure coding practices, vulnerability scanning, and penetration testing.
- Static application security testing (SAST).
AI can analyze code to find potential vulnerabilities before application deployment. - Runtime application self-protection (RASP).
AI-based RASP systems can monitor applications in real-time and detect suspicious behavior.
Cloud Security
Cloud security protects cloud-based assets and services by keeping data private and safe across online infrastructure, applications, and platforms. It is a shared responsibility between the organization and the service provider.
Uses of AI in cybersecurity of the cloud:
- User and entity behavior analytics (UEBA).
AI can analyze user activity in the cloud to identify potential threats or compromised accounts. - Cloud workload protection platforms (CWPP).
AI can continuously monitor and secure cloud workloads from evolving threats.
Identity and Access Management (IAM)
This security system manages user access to IT resources. IAM systems ensure that only authorized users can access specific resources and that their access is logged and monitored.
Possible AI applications:
- Risk-based authentication.
AI can analyze user behavior and context in order to determine the appropriate level of authentication required for access. - User behavior anomaly detection.
AI can detect unusual user login attempts that might indicate a compromised account.
Internet of Things (IoT) Security
This security system is the practice of securing devices connected to the internet, for example these are smart home hubs, wearables, and industrial control systems. IoT security is a growing concern as there are over 17 billion connected devices, and each of them is vulnerable.
Examples of AI uses for IoT:
- AI can analyze data from IoT devices to identify suspicious activity that might indicate a cyberattack.
- Predictive maintenance: AI can predict potential device failures and help prevent security breaches caused by vulnerabilities in IoT devices.
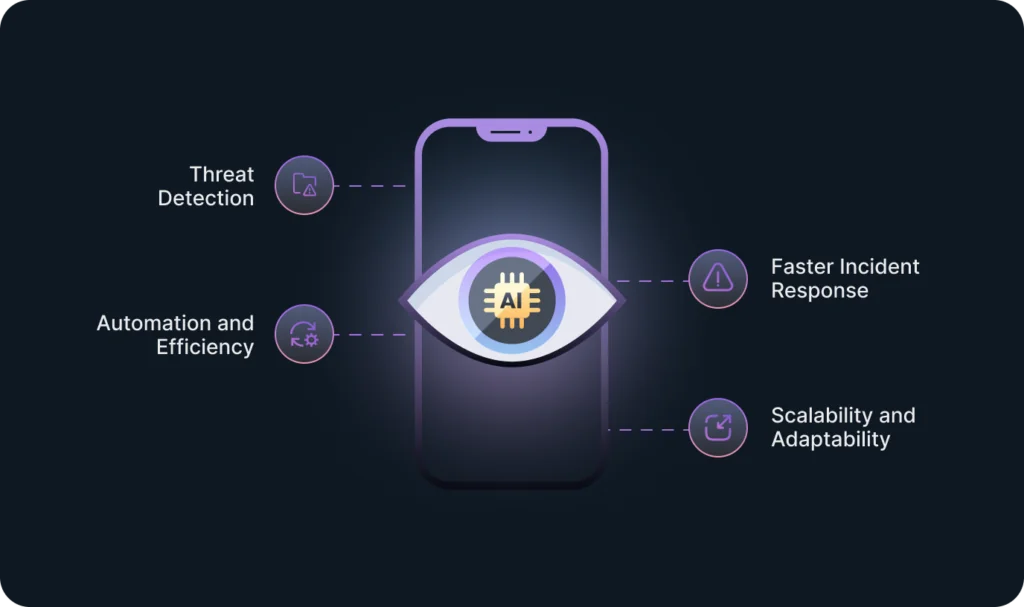
Benefits and Drawbacks of Using AI in Cybersecurity
There can be no doubt that AI can enhance security systems in many ways, for example:
- Detecting threats.
Analyzing vast amounts of data to identify subtle pattern changes that might indicate malicious activity. - Automation.
Automating repetitive tasks such as log analysis. This will increase overall efficiency by allowing the security personnel to focus on other strategic tasks. - Faster incident response.
By automating threat detection and mitigation, AI responds faster to security incidents. - Scalability and adaptability.
AI systems can accommodate growing networks and data volumes. Additionally, AI can adapt to new threats and security landscapes, ensuring continuous protection.
However, you shouldn’t forget that AI itself is still vulnerable. Moreover, using it can introduce additional weaknesses to your system, such as:
- False Positives and Negatives.
AI systems can generate false positives (flagging harmless activity as threats) and false negatives (missing actual threats). - Data bias.
AI algorithms are only as good as their trained data. Biased data can lead to corrupted AI models that miss certain threats or unfairly target specific users. - Insufficient transparency.
AI decision-making processes are quite complex and difficult to understand. Therefore, it might be challenging for us, as users, to debug errors and trust the system’s recommendations. - Security risks of AI itself.
AI systems can be vulnerable to attacks. Malicious actors could potentially exploit vulnerabilities in AI models to launch targeted attacks. - The lack of legal regulation.
The lack of clear regulations around AI use in cybersecurity can create uncertainty regarding liability in case of security breaches or misuse of AI systems.
Bottom Line: How to Implement AI in Cybersecurity?
Eventually, as the technological landscape continues to evolve, new cyber threats will appear, too. However, specialized professionals are always ready to secure your services. Contact our team for a free consultation on how to best implement AI power in your cybersecurity systems!
To learn more about the Devtorium Security Team and the multiple capabilities of AI, check out our other articles: