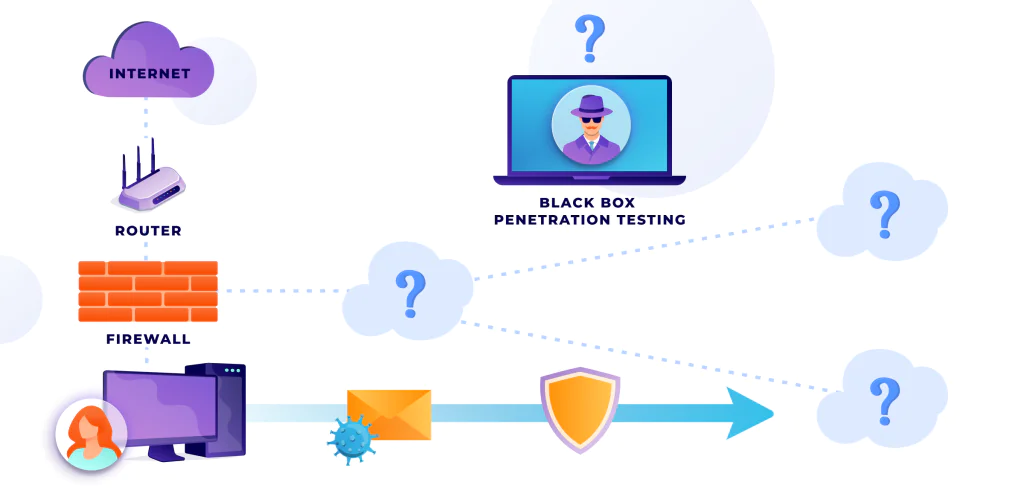
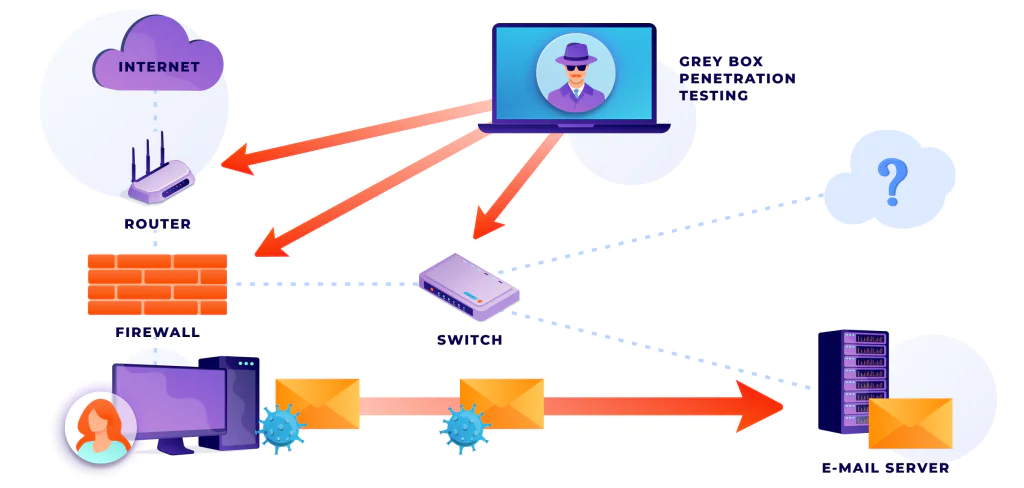
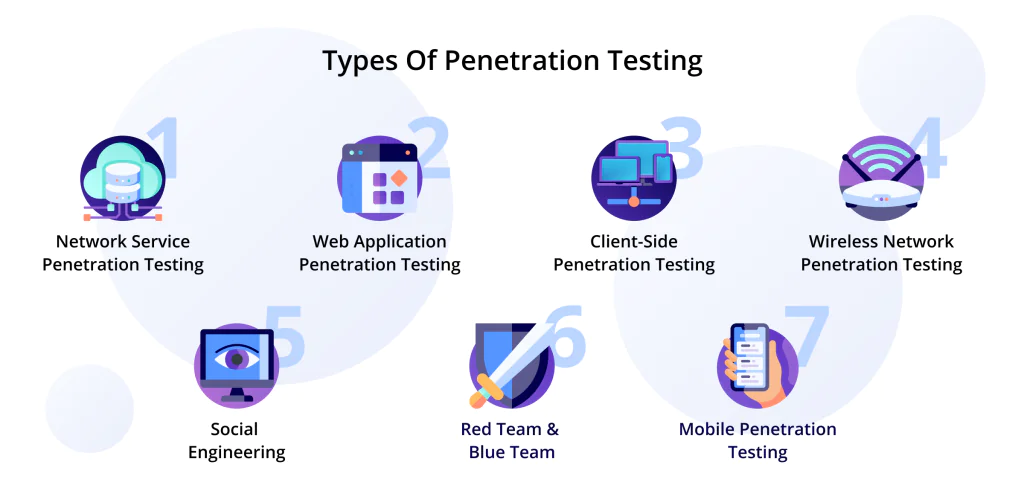
Hiring an IT security services company is a big responsibility because these people will significantly impact your business. Therefore, you need to do a lot of research beforehand to know exactly what to look for.
Today we will discuss the types of IT security services a business needs. This post will help you understand what to consider from the contractor’s list of services and experience.
If you need a reminder of why investing in cyber security services company matters, remember that companies like Equifax and Yahoo lost over $425 and $117 million, respectively, due to data breaches. The number of cybercrimes and losses they cause is growing exponentially. So, today, cyber security should be the highest priority for any business.
Things to Consider When Hiring an IT Security Services Company
Of course, you want maximum benefit for your money, right?
So, the cyber security services company you hire must offer all types of protections that a business needs. Check out the most critical types of IT security services today:
- Network security.
The company you hire must be able to ensure the usability, integrity, and reliability of your entire network. So they do not only protect it from hackers but also prevent problems the users might have accessing the network.
- Internet security.
Your IT security company must protect your browsers and web-based apps. Also, you should find out whether they offer training or find it elsewhere. Employee training is an integral part of the complex measures that ensure your online business security. - Endpoint security.
Endpoint security is device protection. Note that this includes not only desktop computers and laptops used in the workplace but also smartphones and tablets. It primarily relies on device management solutions and malware protection. - Application security.
Bear in mind that application security is literally coded in when the app is in development. That said, it’s possible to increase the security of an existing app after evaluating its code and covering vulnerabilities. But it’s always best to have the highest security level from the start. - Cloud security.
Tools used to ensure cloud services security include, but aren’t limited to, Secure Interner Gateways (SIG), cloud-based unified threat management (UTM), and cloud access security broker (CASB).

How to Hire a Cyber Security Services Company: Other Factors That Matter
When hiring an IT security services company, you need to consider what they can do for you on a broader scale. For example, as a business, you often need to prove that your customers are well-protected. You can do it by displaying certificates from trusted security solutions integrated into your services. In addition, you can educate your clients about the data encryption methods you implement. The security company can provide you with all this.
But businesses dealing with more sensitive data or, for instance, participating in the tendering process need more advanced security verifications. In this case, you can have an IT security services company with an ISO/IEC 27001:2013 Information Security Certificate audit your business. This will allow you to use the internationally-recognized certificate as proof that your company is above reproach. Note that such an audit is a mandatory requirement for some contracts, especially with the government.
Are You Ready to Hire an IT Security Services Company?
You are ready to hire a cyber security services company whenever you even think about starting a business. If you already have a company of your own and no one is providing you with top-notch security services, you are at risk.
Contact Devtorium Information Security Department and arrange an audit right away!
We are an ISO 21007:2013-certified company. Our experts will conduct a detailed audit of all your security systems and protocols and provide a list of suggestions on how to protect your business in the best possible way.