When we established the Devtorium Group of Companies, we aimed for versatility. Today we are introducing Devtorium as a cyber security services company. We understand the value of data protection in the modern world. Therefore, we strive to provide our customers with the best information security audit and management services.
The Devtorium cyber security consulting team uses the PDCA model to help our customers build the most effective defenses. It means that our certified experts can:
- Plan.
Create an ISMS (Information Security Management System) that includes risk management and assets identification. - Do.
Implement and operate the new ISMS. - Check.
Monitor and analyze the ISMS constantly. - Act.
Maintain the ISMS and improve it continuously to protect from emerging threats.
At Devtorium, we deliver full-cycle software product development and maintenance services. To this end, we hold various certifications and are authorized to provide a wide range of information security services. Read the post below to learn what we can do to give your business and data the maximum level of protection.
Devtorium: Cyber Security Services Company with ISO Certification 27001:2013
Morebis Inc. (morebis.net), a part of the Devtorium Group of companies, holds the ISO/IEC 27001:2013 ISMS security certificate. Morebis and Devtorium merged in September 2021, and we have been proud of this deal ever since.
The Morebis Inc. software development team is exceptionally talented and experienced. And now, the Devtorium information security department can provide a higher level of cyber security consulting services to enterprises and other types of businesses.
The ISO certification 27001:2013 enables our team to ‘share’ this certification with customers. So, our clients can boost their credibility by using the certificate icon on their pages as an authorized cyber security services company is auditing them.
We are also eligible to participate in international tenders as this certification is proof of the Devtorium information security audit team’s top-rated skills.
Devtorium Information Security Audit
As a cyber security services company, Devtorium can perform a comprehensive audit of your systems. During this procedure, we are going to analyze the entire system to identify weaknesses in the areas of:
- Physical protection
- Software security
- ISMS standards compliance
By the end of the audit, our experts will be able to guide you in how to bring your company’s security up to the highest standards.
Black Box Assessment
One of the services we offer our customers is Black Box Security Audit. This type of audit works by emulating an external attack to see how the system responds to real-life threats. It’s no secret that cybercriminals are growing bolder by the day. Therefore, the level of threat from attackers and their ingenuity is increasing.
Black Box Audit is an effective response to those threats. Our team developed a unique set of tools that we can use to emulate a wide range of attacks. Moreover, we keep improving it to stay ahead of the emerging threats.
This type of information security audit helps highlight the weaknesses in the client’s existing security system. Also, it enables us to view the potential impact of an attack on the business.
Black Box Assessment is essential because it shows how your protections respond to an attack from a source that doesn’t know anything about the company’s IT structure. Therefore, it helps identify a greater number of system vulnerabilities. As a result of this audit, we are able to develop more robust security solutions for our clients.
Password Audit
We so often take passwords for granted these days. However, it’s crucial to remember that they remain one of the biggest weaknesses of any security system. As a cyber security services company, we make it our business to ensure that our clients use the most efficient password creation and storage methods.
Devtorium will do everything possible within the realm of modern technology to close this route of attack on your data.
Penetration Testing Provided by the Devtorium Cyber Security Services Company
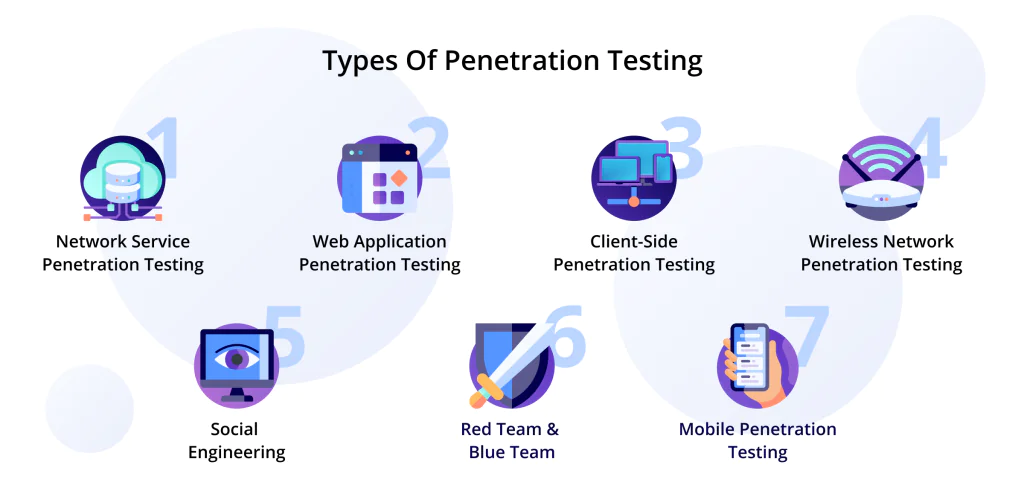
Our cyber security consulting services also include conducting full-range penetration testing of the client’s system. This includes:
- Network service penetration testing
- Web application penetration testing
- Client-side penetration testing
- Wireless network penetration testing
- Social engineering
- Red team & blue team
- Mobile penetration testing
A comprehensive information security audit from Devtorium goes as follows:
- Performing load testing and audit on all of the company’s systems to identify vulnerabilities and risk zones.
- Simulating an attack.
- Finding a weak link in the control systems and modeling an attack.
- Simulating an adversary.
The simulated adversary will follow two possible routes. Number one is an internal attack, for example, a physical attack on the company infrastructure. Another option is acting through employees through bribery, intimidation, extortion, etc. The other way for a simulated adversary to choose is an external attack. It means emulating possible email hacks, network penetration attacks, etc. - Developing a list of recommendations depending on the results of tests and audits.
Once these steps are complete, we can build and maintain a highly reliable ISMS for every client.
Devtorium Cyber Security Consulting and Application Assessment
A part of our cyber security consulting services focuses on web application assessment. Web apps often store a lot of sensitive data, but they can be highly vulnerable to attacks. That’s why they require extensive manual testing in order to develop the best protection.
After performing these tests, we would be able to advise how to increase the security maturity of the app. In addition, we will offer solutions to limit its inherent security weaknesses.
We use various methods to identify vulnerabilities during our web app information security audit. We try to find weaknesses at every stage of the application life cycle: design, development, deployment, upgrading, and maintenance. In addition, we study possible app design defects that can turn into vulnerabilities over time.
Our ultimate goal is to find, fix, and, most importantly, prevent weaknesses. Looking into the future is what we do at Devtorium. Our motto is to future-proof our customers’ businesses to help them succeed in today’s volatile economic conditions.
If you want to ensure that your company’s cyber security performs to the highest standards, contact us and set up a consultation now!







