If you wonder whether investing in information security and penetration testing is worth it, consider that cybercrime is expected to cost $10.5 trillion by 2025. So, top-notch cybersecurity is invaluable if you want to minimize the risk of losing a massive part of your business money. Your IT infrastructure will require extensive testing to create an efficient information security system.
During penetration testing, auditors simulate all kinds of attacks. Therefore, they use different approaches depending on the level of information available to the expert. To make the conditions close to real life, testers might not have any ‘insider’ info, like any external hacker. Using this criterion, experts distinguish three main approaches to pen tests: black, white, and gray box.
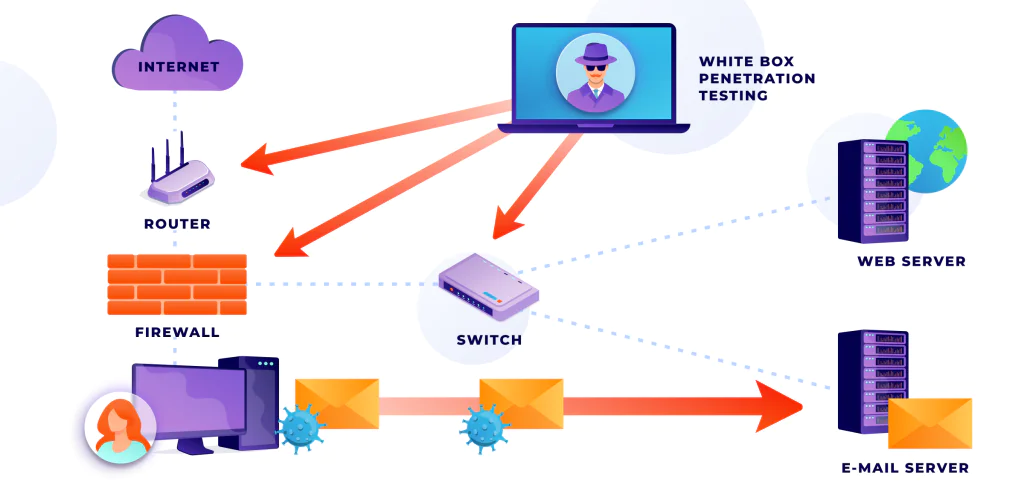
White Box Penetration Testing
White box pen testing is when the tester has access to complete information about the source code and environment. Basically, the pen testing team knows all there is to know about the system. Therefore, they can perform a most comprehensive study of its weaknesses. This analysis includes assessing areas such as code quality or system design.
Other names for white box testing include internal penetration testing or clear/glass box testing. The names indicate that this audit aims to study the entire system in-depth. Such a comprehensive analysis is rather expensive. Each area of the whole security infrastructure must be tested thoroughly. Therefore, on average, white box penetration testing can take two or three weeks.
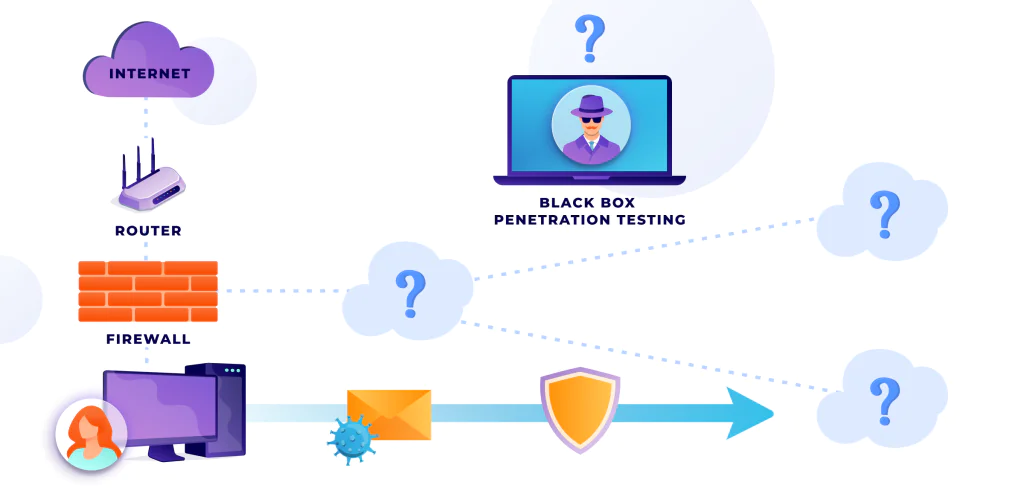
Black Box Penetration Testing
Black box, otherwise called external penetration testing, is an approach used to simulate an attack from outside. The tester has very little, if any, information about the system. This approach allows running tests in a setting closest to a real-life hacker attack.
The cost of these penetration tests can vary greatly depending on the business’s IT infrastructure and requirements. However, it’s important to note that black box penetration testing can take as many as six weeks. In addition, these audits require extensive planning and creating a detailed report on how to address all system vulnerabilities.
The attack can be complex, and the tester will use all possible means to break into the system. To perform a quality black box audit, testers must have specialist experience. Look for certified professionals only.
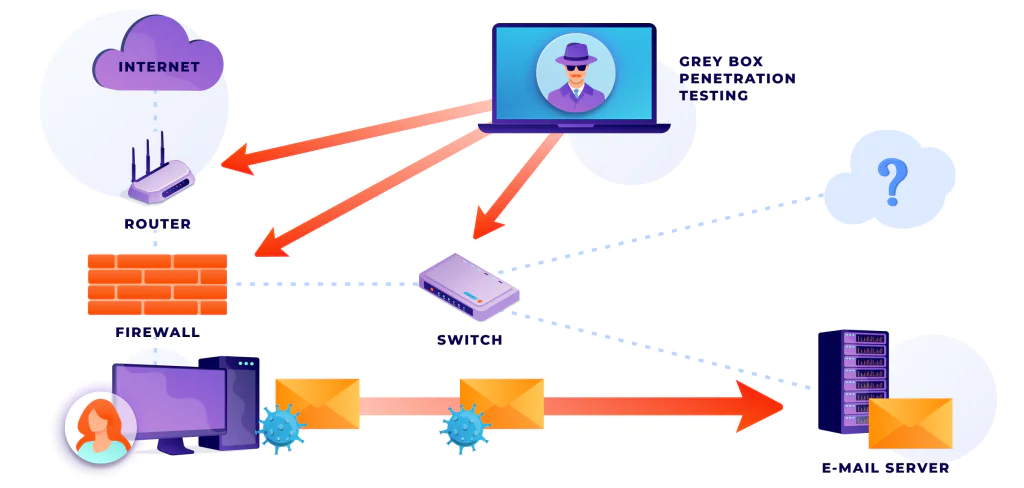
Gray Box Penetration Testing
Gray box penetration testing is a mix of black and white. First, the tester has partial information and access to the system. From there, they will use a wide range of techniques and tools to break into it. One common gray pen testing scheme is giving the tester standard user privileges.
Note that for this approach the customer might request a specific set of conditions. For example, trying to get access to the application source code from the position of a registered user account.
Due to this methodology, gray penetration testing is more precisely targeted. So, the customer might use their budget most efficiently. In addition, this testing allows the creation of particular recommendations on how to get rid of the identified vulnerabilities.
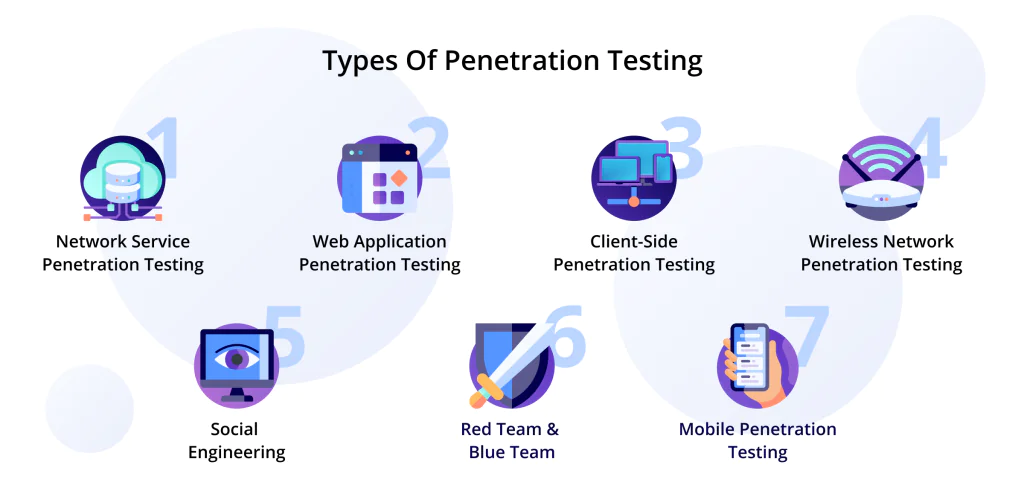
Penetration Testing Types, Tools, and Methods
White, black, and gray are approaches that cybersecurity experts use during an audit. Those approaches are realized through a set of pen tests that can be divided into types based on targeted areas.
Network service testing
Network service penetration testing analyzes the infrastructure of the network to find vulnerabilities that can be exploited. This type of testing studies servers, firewalls, routers, printers, switches, workstations, etc. The purpose of this test is protection against the most common threats that target networks. Those include:
- Router attacks
- DNS attacks (zone transfer attacks and switching/routing attacks)
- Firewall misconfiguration or bypass
- FTP/SMTP attacks
- SSH attacks
- Database attacks
- Proxy server attacks
- Man In The Middle (MITM)
- Unnecessary open ports
Network services are critical for any business. Therefore, it’s imperative to ensure your absolute security in this area.
Application testing
Apps can perform a multitude of tasks, both within the business and for its interactions with customers. However, they also serve as inherent security weaknesses, especially web-based apps. Therefore, penetration testing of each app becomes a necessity.
This type of testing will use a wide range of methods to try breaking the application from every entry point. Therefore, these tests must be highly targeted and detailed to ensure no weakness is missed. In the end, the team of auditors should provide a detailed report. It must list all the vulnerabilities and rate them by the threat level. Also, they must offer solutions for each issue.
Wireless network testing
Wireless penetration testing focuses specifically on the WiFi part of the business’s IT infrastructure. Today this testing covers not only laptops, smartphones, and tablets but also all connected IoT devices. Note that this type of audit should be performed on-site.
Important points to consider during this type of pen testing include:
- Identifying every single entry point.
- Analyzing the level of encryption at each point.
- Assessment of the systems used for monitoring for possible unauthorized users.
- Studying the network configuration.
- Evaluating current protection measures.
- Checking if all entry points use the WPA protocol.
Social engineering
Social engineering pen testing looks into the possibility of an outside agent using different methods to trick sensitive information out of the users. For example, one such threat is cons that aim to persuade you to give up bank login information. Bear in mind that most cyberattacks use social engineering at some point in their schemes.
Penetration testers use the following simulated attacks and tricks to run this audit:
- Gifts
- Phishing
- Pre-texting
- Smishing
- Name dropping
- Vishing
- Imposters
- Dumpster-diving
- Eavesdropping
Client-side penetration testing
Finding any weaknesses in client-side apps is a must to identify specifically targeted cyberattacks. This type of testing is used to fight against threats like:
- Malware infections
- HTML injections
- Cross-site scripting attacks
- Hijacked forms
- Clickjack attacks
- Open redirections
- Cross-origin resource sharing (CORS)
Red team & blue team
Red and blue team penetration testing audits the system using two different types of simulations. Red teams focus on offensive defense. It means that they simulate external attacks. Meanwhile, blue teams are pure defense. Therefore, they clash with the red teams, and each side tries to find weaknesses in the other.
The testing environment is completely controlled. However, it’s as close as you can get to an attack from real hackers. As a result, it can provide valuable insights and help design an effective cyber security infrastructure.
Mobile penetration testing
Penetration testing specialists will use manual and automated testing tools to find weaknesses specifically in mobile apps. Those are always high-risk. Also, they often use multiple third-party software integrations. Therefore, the number of possible weaknesses increases.
Extensive penetration testing will enable auditors to find any vulnerabilities and issues with:
- Authentication
- Authorization
- Cryptography
- Session management
In Conclusion: Which Testing Type Does Your Business Need?
There can be no doubt that penetration testing is essential if you want to ensure the security of your business in the digital age. However, as you’ve seen, information security testing can be highly varied. Therefore, the most efficient way to provide your business with the best defenses is to consult an experienced cyber security services company.
Expert auditors will be able to assess your business’s current cybersecurity infrastructure and needs. Then, they can use this information to develop a plan that will give you the maximum level of protection for any budget. If that is your goal, contact us and make an appointment with Devtorium information security experts anytime!